An ethical hacker follows a similar process to that of a malicious hacker to gain and maintain access to a computer system. The process of a typical attack scenario can be broken down into five distinct phases, which are described in this article.
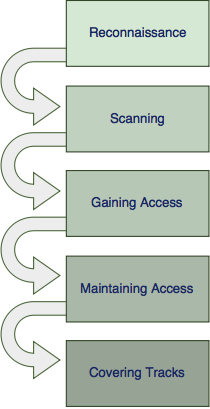
Phase 1: Reconnaissance

The first phase is all about gathering preliminary data on the target and learning as much as possible about how it operates. Reconnaissance can be performed actively or passively and sets the basis for further planning the attack. The target usually does not notice anything during this phase.
The used methods typically include identifying the target and discovering the target IP address range, network, domain name, mail server, DNS records, etc... Depending on the target and approach, this may also include non-technical information like employee registers, organizational charts and company relations.
Phase 1 techniques may include the following:
- Internet sources
- Social engineering
- Dumpster diving
- Observation
Traditional burglar
When drawing a parallel with a traditional burglar trying to steal from a rich person, this phase would involve finding out where the person lives, at what times he usually is at home and the type of security system or fence he has.
Phase 2: Scanning
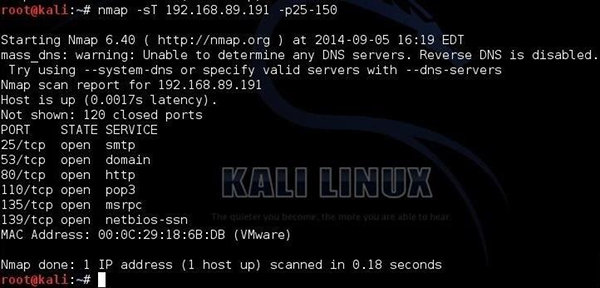
In this phase, the information gathered during the reconnaissance phase is used to scan the perimeter and internal network devices looking for weaknesses. This phase requires the use of technical tools to gather further intelligence on the target and about the systems that they have in place.
It includes scanning the target for services running, open ports, firewall detection, finding vulnerabilities, OS detection, etc...
Phase 2 techniques may include the following:
- Port scanners
- Vulnerability scanners
- Network mappers
Traditional burglar
In this phase, a burglar would typically check the locks for complexity or see if there are any open windows he may be able to reach.
Phase 3: Gaining access
In phase 3 the attacker would exploit a vulnerability to gain access to the target. This typically involves taking control of one or more network devices to extract data from the target or use that device to perform attacks on other targets.
Some examples of methods to gain access are:
- Abusing a username/password that was found
- Exploiting a known vulnerability
- Breaking into a weakly secured network
- Sending malware to an employee via E-mail or a USB stick on the parking lot
Traditional burglar
This is the phase where the traditional burglar would actually enter the house via an open window.
Phase 4: Maintaining access
After having gained access, the attacker will now need to maintain access long enough to gather as much data as possible or to enable himself to return at a later time.
In order to maintain access for a longer time, the attacker must remain stealthy to not get caught using the host environment.
Some examples of techniques used in this phase:
- Privilege escalation
- Installation of a backdoor or remote access trojan
- Creating own credentials
Traditional burglar
In this phase, the burglar may create a copy of a found key or disable the alarm system long enough for him to extract the goods.
Phase 5: Covering tracks

In the final phase, the attacker will take steps necessary to hide the intrusion and any controls he may have left behind for future visits.
Any changes that were made, installed trojans, backdoors, escalated authorizations, etc. must return to a state in which the attacker's presence cannot be recognized by the network's administrators.
Some examples of covering tracks:
- Remove logging
- Exfiltration of data via DNS tunneling or steganography
- Installation of rootkits
Traditional burglar
In this phase the burglar will wipe the fingerprints from anything he may have touched.
